In an age where technology plays a crucial role in our lives, the threat landscape for cyberattacks has expanded exponentially. While we often think of hackers as exploiting technical vulnerabilities, one of the most potent tools in their arsenal doesn’t rely on code or complex algorithms. It’s the art of social engineering.
Social engineering is a manipulative technique used by individuals or groups to deceive others and gain access to confidential information, systems, or physical spaces. It relies on exploiting human psychology and behavior rather than technical vulnerabilities.
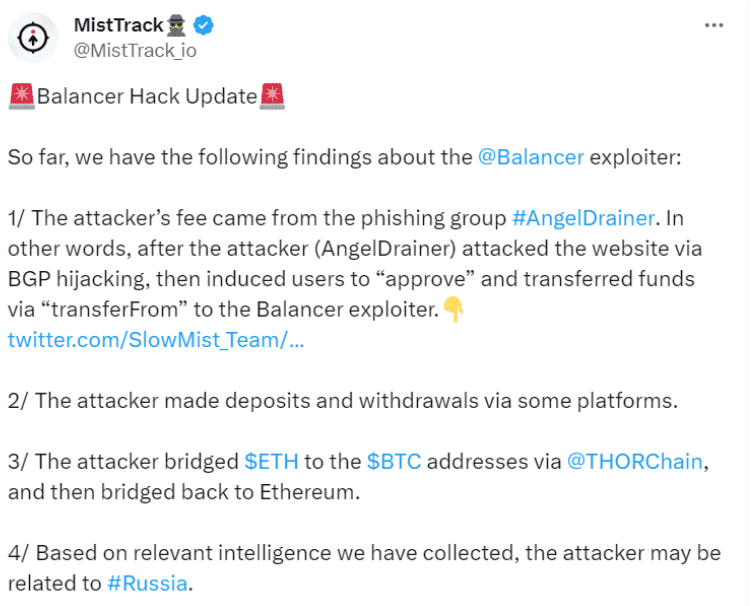
Balancer, one of the renowned Ethereum-based automated market makers, recently suffered a social engineering attack on its DNS which resulted in approx. $238000 worth of crypto losses. Balancer shared a post on its Twitter handle on September 20 to confirm its DNS hijacking.
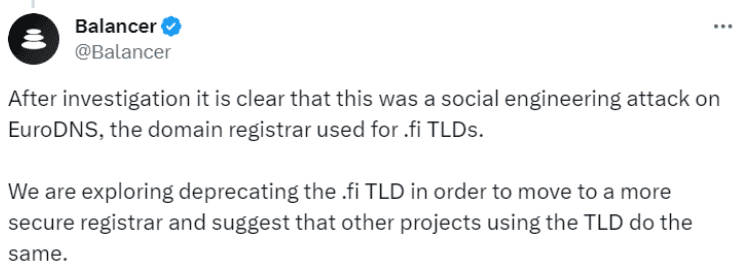
Just after sharing the confirmation on the social media platforms, Balancer stated that they’ve successfully secured the domain and brought it back under Balancer DAO’s control.
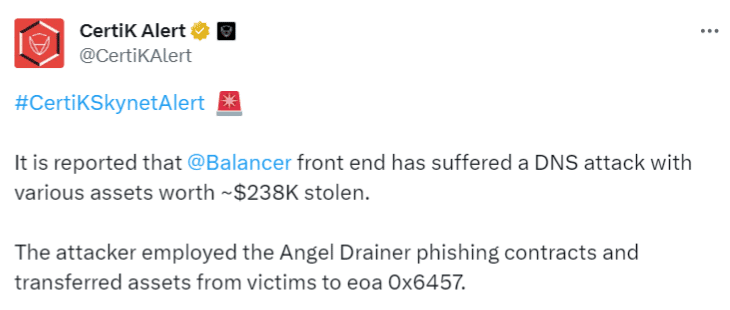
Certik, a pioneer in Blockchain technology, stated the primary reason behind this social engineering attack.
According to another report shared by SlowMist, a top Blockchain security firm, the attacker belongs to Russia and executed the attack through Border Gateway Protocol Hijacking: A cyberattack where malicious actors manipulate BGP routes to reroute internet traffic through their networks.
Protecting against social engineering attacks is essential to maintain the trust and stability of DeFi platforms. Such attacks pose severe financial risks and undermine trust in the DeFi ecosystem. Preventing DNS hijacking ensures that users interact with genuine services, reducing the likelihood of fraud, theft, or disruptions. It upholds the sector’s reputation for security and reliability, encouraging investor confidence and fostering sustainable growth in the decentralized financial space.
Types of Social Engineering Hacks
- Phishing Attacks
Attackers send deceptive emails or messages that appear legitimate to trick recipients into revealing personal information, login credentials, or clicking on malicious links.
- Pretexting
This involves creating a fabricated scenario or pretext to gain someone’s trust and extract information or access. For example: impersonating a co-worker or service technician to request sensitive data.
- Baiting
Cybercriminals offer something enticing, such as a free download or a USB drive, infected with malware. When the victim takes the bait and uses the item, their device becomes compromised.
- Tailgating
Also known as “piggybacking,” this technique involves physically following an authorized person into a secure area by pretending to be an employee or contractor.
- Quid Pro Quo
Attackers offer a service or assistance in exchange for sensitive information or access. For example, offering IT support in exchange for login credentials.
- Email Spoofing
Sending emails that appear to come from a trusted source, like a bank or government agency, to trick recipients into providing sensitive information.
- Watering Hole Attacks
Attackers compromise websites frequented by their targets, infecting these sites with malware to infect visitors’ devices.
Motives Behind Social Engineering Hacks
Social engineering hacks occur for various reasons, all of which revolve around exploiting human psychology and behavior for malicious purposes. Some primary motives behind social engineering hacks include:
- Data Theft
Attackers aim to steal sensitive information, such as financial data, login credentials, personal identification details, or proprietary business data, which they can use or sell for financial gain.
- Espionage
Nation-state actors or corporate spies use social engineering to gather intelligence, trade secrets, or classified information to gain a competitive advantage or further political agendas.
- Financial Gain
Hackers may target individuals or organizations to trick them into making financial transactions or divulging financial information, leading to monetary losses.
- Network Access
By deceiving employees or individuals with privileged access, attackers can gain entry to corporate networks, systems, or physical premises, facilitating further attacks or data breaches.
- Reputation Damage
Some attackers engage in social engineering to damage an individual’s or organization’s reputation by spreading false information or engaging in activities that tarnish their image.
- Testing Security Defenses
Ethical hackers and security professionals may employ social engineering techniques to assess an organization’s vulnerabilities and improve security measures.
Prevention Techniques to Social Engineering Hacks
Preventing social engineering hacks requires a combination of awareness, education, and proactive security measures. Here are some effective prevention techniques:
- Phishing Awareness
Teach users to scrutinize emails, verify sender identities, and avoid clicking on suspicious links or downloading attachments from unknown sources.
- Employee Training
Provide regular security awareness training for employees to recognize social engineering tactics, including phishing emails, pretexting, and impersonation.
- Two-factor authentication (2FA)
Implement 2FA for critical systems and accounts to add an extra layer of security even if login credentials are compromised.
- Strict Access Controls
Limit access to sensitive information and systems on a need-to-know basis. Regularly review and update permissions.
- Verified Communication
Encourage employees to verify requests for sensitive information or financial transactions through a trusted, separate communication channel when in doubt.
- Secure Password Policies
Enforce strong password policies, including regular password changes, and use a password manager to generate and store complex passwords.
- Awareness of Social Engineering Tactics
Educate employees about common social engineering tactics and warning signs, such as urgent requests, misspelled email addresses, or unexpected requests for information.
- Security Updates
Keep software, operating systems, and security software up to date to patch vulnerabilities that attackers might exploit.
- Regular Backups
Regularly back up critical data and systems to ensure quick recovery in case of a successful social engineering attack.
- Vendor and Third-Party Assessment
Assess the security practices of third-party vendors and partners, as they can be a weak link that attackers exploit.
- Physical Security
Maintain physical security measures to prevent unauthorized access to facilities and prevent tactics like tailgating.
- User Behavior Analytics
Implement user behavior analytics tools that can detect abnormal patterns of access or behavior indicative of social engineering attacks.
- Encryption
Use encryption for sensitive data both in transit and at rest to protect it from interception or theft.
Conclusion
Preventing social engineering hacks is an ongoing effort that involves both technology and human vigilance. By implementing these prevention techniques and maintaining a strong security posture, organizations can significantly reduce their vulnerability to social engineering attacks. Stay vigilant, educate yourself and your employees, and always verify the legitimacy of requests for sensitive information or get in touch with a renowned smart contract audit company to know more about such hacks.