Step into 2026, where privacy equals ownership and every on chain choice speaks louder than glossy marketing. If you care about safeguarding capital and operational discretion, understanding how no-KYC wallets actually work stops being academic and becomes strategic. In this piece we peel back the curtain on seed generation, private key custody, transaction signing and the privacy scaffolding that seasoned investors use to reduce exposure while maintaining liquidity. You will see how routing, coin control and hardware anchors fit into real-world flows and why technical design decisions matter when assessing risk. Along the way we reference practical signals from the market and implementation patterns that matter to treasury managers and product leaders. For enterprises exploring cryptocurrency wallet development or evaluating custody models, this guide lays out a clear, evaluative view so you can choose with confidence.
What are No-KYC Crypto Wallet Solutions?
No-KYC crypto wallets are self-custodial applications and devices that let users control private keys and transact on public blockchains without submitting identity documents. For privacy-first users in 2026, these wallets reduce the number of centralized data touchpoints and speed up onboarding while keeping full ownership of funds. They appear as mobile apps, browser extensions, desktop clients, and hardware devices. Some wallets offer privacy tools and advanced coin control, while others prioritize broad multi-chain access without collecting personal data. These tools do not remove legal obligations when interacting with regulated on-ramps or exchanges, so the right wallet depends on your threat model, asset mix, and operational needs.
How Do No-KYC Crypto Wallet Solutions Work?
No-KYC cryptocurrency wallet apps function as self-custodial tools that let users create and control cryptographic keys without submitting identity documents. At first, installing the wallet generates a seed phrase and derives private keys, which remain stored locally and never leave the device. When you initiate a transaction, the wallet constructs and signs it using those keys, then broadcasts the signed transaction to the network via nodes or relayers.
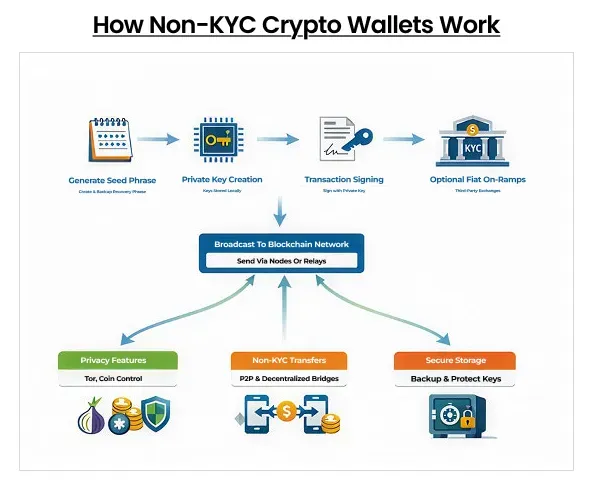
Many privacy-focused Web3 crypto wallets optionally route traffic through networks like Tor to obscure IP metadata, and they offer address management, coin control, or mixing tools to reduce on-chain linkability. Third-party fiat on-ramps and exchanges operate separately and may require KYC, so private flows rely on non-custodial bridges or peer-to-peer channels. Secure seed backup, firmware updates, and disciplined operational habits complete the lifecycle from setup to long-term custody.
Our Methodology: How Did We Vet These No-KYC Cryptocurrency Wallets?
We tested candidate wallets against 5 practical criteria that matter to privacy-focused users and enterprise buyers:
1. Security model and private key custody
2. Built-in privacy features and optional obfuscation tools
3. Real-world asset and chain support for 2026 use cases
4. Usability and developer ecosystem for integrations
5. Costs, third-party KYC touchpoints, and on-ramp exposure
We combined hands-on testing, documentation audits, and recent market signals. Special attention was given to wallets that explicitly maintain a non-custodial model and do not require identity verification to create or use an account. Where privacy tools intersect with legal risk, we flagged regulatory developments and operational mitigations. Now let us scroll through the blog to explore these five major names in the market.
Top 5 No-KYC Crypto Wallets for Privacy-Focused Users in 2026
1. MetaMask
MetaMask remains the go-to multichain browser and mobile wallet for users who need seamless access to DeFi, NFTs, and cross-chain tools while retaining self-custody. It generates a secure seed phrase locally, supports custom networks, and connects to dapps through WalletConnect and browser integration. Developers and enterprise teams often study its extensible architecture when planning digital wallet app development projects because it demonstrates how to balance usability, plugin ecosystems, and non-custodial security. For investors, MetaMask offers the combination of broad protocol reach and an active developer community that drives rapid feature adoption, making it a pragmatic choice for private on-chain activity.
2. Trust Wallet
Trust Wallet is a mobile-first wallet solution built for broad token coverage and simplified user flows that keep private keys in the user’s control. It supports dozens of blockchains and includes in-app swaps, staking, and a DApp browser, which makes it attractive for retail and institutional pilots that need wide asset support without forcing identity collection at wallet creation. Its flexible integration model and strong mobile UX also make it suitable when enterprises evaluate a white-label crypto wallet platform or custom integrations for client onboarding. For investors seeking ease of use paired with non-custodial security, Trust Wallet provides a low-friction path into multi-chain strategies.
3. Wasabi Wallet
Wasabi is a desktop Bitcoin wallet designed for users whose primary requirement is on-chain anonymity and provenance minimization. It builds wallet keys locally, routes traffic over Tor by default, and facilitates trustless CoinJoin transactions that mix funds to break on-chain linkability. Advanced coin control and clear privacy options let experienced users separate funds, avoid address reuse, and tailor mixing sessions to their threat model. Wasabi’s open-source design and auditability make it attractive to investors and privacy advocates who need verifiable privacy guarantees. This wallet is best suited for users who accept greater operational complexity in exchange for stronger on-chain anonymity.
4. Samourai Wallet
Samourai is a mobile Bitcoin wallet engineered around real-world privacy tooling, including Whirlpool mixing, sophisticated coin control, and stealth addressing features. It emphasizes operational privacy by minimizing metadata leakage and providing tools for staged mixing and consolidation that reduce traceability across transactions. Samourai also offers features tailored to active users who want mobile privacy controls alongside manual funding workflows. Investors examining privacy-first custody models will value Samourai’s focus on practical anonymity hygiene. Note that such advanced privacy capabilities can attract regulatory attention in some jurisdictions, so enterprises should assess compliance exposure before embedding these flows into commercial products.
Build The Right Non-KYC Wallet With The Right Provider
5. Ledger (Hardware Wallet)
Ledger provides offline key custody through hardware devices that isolate private keys inside a secure element and require physical confirmation to sign transactions. This architecture removes cloud exposure and pairs cleanly with non-custodial cryptocurrency wallets to execute privacy-preserving workflows while keeping keys cold. Ledger’s ecosystem now includes transaction verification surfaces that display full details so users can detect malicious signing attempts. For institutional or high-net-worth investors, Ledger devices provide a best-practice anchor for long-term holdings and multi-signer setups, enabling high-assurance custody without centralized identity capture during wallet creation.
Head-to-Head: Top Crypto Wallets with No KYC At a Glance
| Wallet | Security | Asset Support | Key Features | Cost |
| MetaMask | Software, the user holds keys locally | Ethereum, EVM chains, tokens via custom RPC | WalletConnect, DeFi integrations, browser extension | Free; network fees apply |
| Trust Wallet | Mobile-only, self-custody | Multi-chain: EVM, BSC, Solana via updates | Built-in DApp browser, staking, in-app swap | Free; swap fees vary |
| Wasabi Wallet | Desktop, open source, CoinJoin via coordinator-less protocols | Bitcoin only | CoinJoin mixing, Tor routing, coin control | Free; mixing fees and coordinator fees may apply |
| Samourai Wallet | Mobile, privacy-first, strong coin control | Bitcoin only | Whirlpool mixing, stealth features, paynym support | App free; mixing fees apply |
| Ledger (hardware) | Hardware secured keys, secure element | Bitcoin, Ethereum, >10,000 tokens via apps | Physical confirmation, firmware security, integrate with wallets | Device purchase cost; software is free |
Why Did These 5 Make It to The Top No-KYC Crypto Wallet List?
Multi-chain, usability, and privacy cannot always be perfectly aligned. MetaMask and Trust Wallet deliver the best bridge to DeFi and token ecosystems without KYC. Wasabi and Samourai provide focused, mature Bitcoin privacy tooling. Ledger secures keys offline and pairs with software wallets when users want a hardware anchor. Together, they represent the pragmatic spectrum of privacy-first options in 2026.
Conclusion
Privacy-first crypto wallets give users control and reduce unnecessary exposure of personal data, but they are not a substitute for regulatory compliance when using fiat rails. If you want to build or integrate private wallet capabilities into a product, Antier provides end-to-end blockchain wallet app development, AI-assisted security reviews, and enterprise-grade deployment. Our team blends deep protocol knowledge with practical implementation experience to design wallets that meet both security demands and user expectations. Reach out to discuss architecture, compliance-aware privacy features, or a white-label solution tailored to your enterprise needs.
Frequently Asked Questions
01. What are No-KYC crypto wallets?
No-KYC crypto wallets are self-custodial applications and devices that allow users to control their private keys and transact on public blockchains without submitting identity documents, enhancing privacy and ownership.
02. How do No-KYC crypto wallets function?
No-KYC crypto wallets generate a seed phrase and derive private keys that are stored locally. They sign transactions using these keys and broadcast them to the network, often incorporating privacy features like traffic routing through networks like Tor.
03. What should enterprises consider when choosing a No-KYC wallet?
Enterprises should evaluate their threat model, asset mix, and operational needs, as the right No-KYC wallet depends on these factors and may include features like privacy tools, coin control, and multi-chain access.