Introduction
Cryptocurrency exchange development in 2025 is not for the faint of heart. Flashy UI/UX, AI gimmicks, and airdrops may catch eyes, but without a robust backend, they’re just decorations and distractions. Crypto hackers don’t care about dashing dashboards or smooth onboarding flows. They’re ruthless, cunning, and evolving faster than ever.
If you’re running a cryptocurrency exchange software or planning to launch one soon, your platform could be the next big thing, but it could also be the next big target.
Biggest Crypto Exchange Hacks of 2025 (So Far)
2025 appears to be the worst year for crypto thefts yet, as it is only six months into the year, and $2.17 billion has been stolen across CEXs, DeFi platforms, bridges, and wallets. It was already 17% more value lost than in all of 2022, which was the worst year on record previously. Exchanges are under siege like never before. One ignored patch, one missed audit or unaudited contract, or one outdated security layer, and you’re not just risking money, you’re playing with fire. Treating security as an afterthought in cryptocurrency exchange software development today means handing hackers the matches yourself.
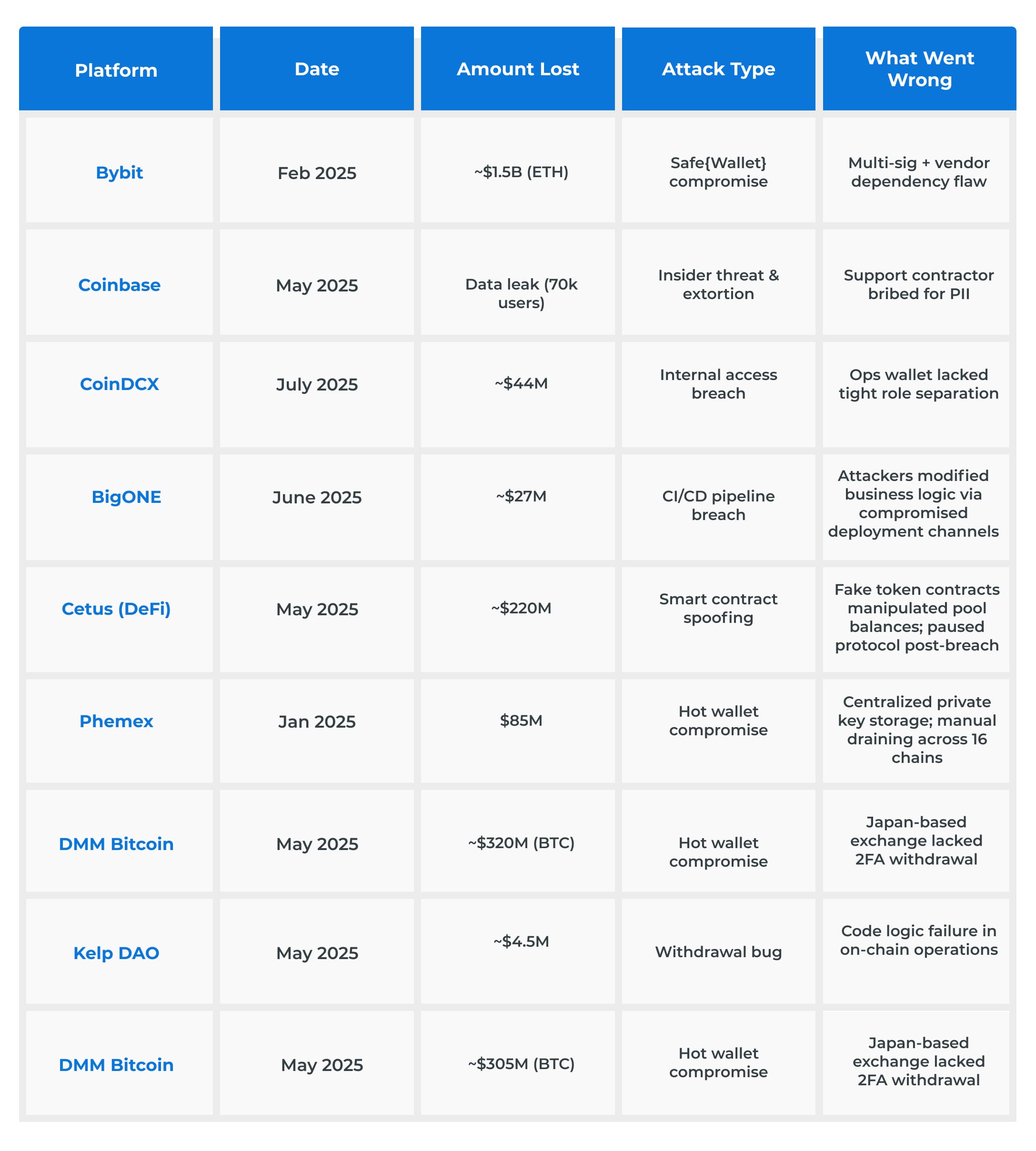
What are the Key Crypto Exchange Attack Trends in 2025? (Summarized)
- North Korean State Actors: Lazarus Group linked to Bybit ($1.46B) and DMM Bitcoin ($320M) heists, using advanced social engineering.
- Insider Threats: Coinbase (contractor bribery) and BigONE (CI/CD compromise) demonstrate rising risks associated with third-party dependencies.
- Hot Wallet Vulnerabilities: 80% of exploits targeted hot wallets, often due to poor key management or segmentation flaws.
- Cross-Chain Laundering: Stolen funds (e.g., CoinDCX, DMM Bitcoin) routed through bridges/mixers like Tornado Cash.
- Cold Wallet Invincibility Myth Debunked: The Bybit hack showed that multi-sig processes can be compromised via vendor tools.
These crypto exchange hacks didn’t happen in dark alleys; they were public, brutal, and largely preventable. Security-focused cryptocurrency exchange development may seem challenging, but it’s still possible if you learn from the mistakes of hacked trading platforms. Let’s now break down the top crypto hacks and how cryptocurrency exchanges can protect themselves against these biggest threats.
How to Protect Your Crypto Exchange from 2025’s Biggest Hacks
Just a few things taken care of during your cryptocurrency exchange software development, and you might save your exchange from these hacks that don’t just take the money away, but also the platform’s reputation. It takes away what exchanges invest millions and years to build.
1. ByBit’s 1.5B Hack:
On February 21st, 2025, North Korea’s notorious hackers pulled off what they called the largest cryptocurrency theft in history. They infiltrated the Dubai-based exchange’s cold wallet system, supposedly the most secure storage method, and drained 400,000 ETH worth $1.5 billion. The attack bypassed multisig protections through sophisticated phishing and possible supply chain compromises.
Secure Crypto Exchange Platform Development Tip: Even cold wallets can be hacked through third-party vendors. Secure supply chain and infrastructure dependencies, as multisig isn’t enough if external partners are vulnerable.
Exchange Security Checklist:
- Host critical tools in-house or audit vendors regularly
- Segment production environments
- Simulate compromise drills quarterly
- Layer multisig with time locks
2. Coinbase Data Breach
Even millions can’t buy users’ trust, and sometimes all it takes is an insider extortion, and those billions of dollars spent on cryptocurrency exchange development could be questioned. A social-engineering exploit hit Coinbase’s support staff. Attackers paid overseas contractors for user account data (names, addresses, emails). Coinbase says they did not get passwords, but the breach could cost as much as $400 million.
Not A Secure Exchange Development Takeaway: This incident underscores the insider/contractor risk, not just technical centralized cryptocurrency exchange development flaws. So, sometimes the weakest link can be your staff and not your cryptocurrency exchange development company.
Exchange Protection Checklist:
- Strict vetting and rotating stellar contractors
- Enforce least-privilege access
- Deploy behavior analytics tools (detect abnormal data access)
- MFA and session timeouts in support tools
3. CoinDCX’s 44 Million Loss:
CoinDCX, India’s largest exchange, was exploited for $44million. Attackers compromised internal operational accounts, and the regional giant’s weak immunity was exposed to the world. The compromised internal credentials allowed unauthorized access to wallet systems without triggering security thresholds. The attacker drained funds across multiple assets before detection.
Security-Focussed Crypto Exchange Platform Development Takeaway: If internal accounts can move funds in centralized exchanges, they can also be attacked. Internal risk equals business risk.
Secure Exchange Development Checklist:
- Enterprise-grade RBAC with transaction approvals
- Daily reconciliation & anomaly alerts
- Air‑gapped vaults for internal ops
- Bug bounty programs
- Internal red team reviews
4. Nobitex’s $90 M Political Hack
Iran’s largest exchange, Nobitex, was hit by a politically motivated hack. A group called “Predatory Sparrow” stole nearly $90 million by using stolen admin credentials and private keys. Funds were even sent to burn addresses with anti-government messages. Nobitex responded by moving all major assets to cold storage and working with authorities and forensic firms to trace any recoverable funds.
Not A Secure Exchange Development Takeaway: Geopolitical hacks are real. Sometimes, your cryptocurrency exchange software development company has done a great job at protecting your trading platforms, but threat actors may hit your exchange anyway to further politics, not profit.

Security Layer Enhancement Checklist
- Geo-fencing and country risk scoring
- WAF and real-time blockchain monitoring
- On-chain firewall to freeze suspicious withdrawals
- Public incident timeline for user trust
Additional Tip: Your tech partner might not be responsible for the hack, but they can still help you prevent these geopolitical hacks with security-first crypto exchange platform development.
5. Phemex 85M Hack:
Singapore’s Phemex exchange lost about $85 million when attackers drained 16 hot wallets. Halborn’s investigation found the root cause was compromised private keys (likely held in one place). The hackers drained funds chain by chain, probably swapping assets to avoid freezes.
Security Takeaway For Your Exchange: No amount of transparency can undo damage caused by weak private key management. Exchanges must assume that any exposed hot wallet will be targeted and eventually breached.
Secure Cryptocurrency Exchange Development Checklist
- Use multi-sig cold wallets for reserves
- Cap hot wallet amounts with time-locked limits
- Flag abnormal withdrawals instantly
- Rotate keys regularly, especially after staff changes
- Run live audits on key systems
- Practice breach drills & rollback plans
- Use custodians (Fireblocks, Anchorage) for big assets
- Alert users on critical threshold events
6. Cetus 220M Hack:
Cetus, which is a decentralized exchange on the Sui blockchain, lost roughly $220 million when attackers used fake token contracts to trick the system. In this exploit, spoofed token metadata bypassed security checks and allowed massive withdrawals, marking a huge risk for emerging decentralized cryptocurrency exchange software development projects.
Security Takeaway for DEXs: Fake or spoofed tokens can slip into DEX interfaces and trading UIs by mimicking legitimate asset metadata. Without strict validation, users might end up buying worthless tokens or interacting with malicious contracts.
DEX Security Checklist:
- Whitelist known tokens
- Cross-verify contract addresses
- Use token standards that include built-in authentication (e.g., EIP-2612)
- Add circuit breakers to pause trading for unknown or unverified assets
- Set backend validation rules to confirm on-chain metadata (name, symbol, decimals), don’t only rely on the frontend
- Restrict high-value actions to allowlisted tokens/contracts
Now, whether you plan to build your security-first centralized or decentralized cryptocurrency exchange, you know how not to make headlines that are a threat to your exchange’s existence.
Your Exchange Doesn’t Only Need A Bigger Marketing Budget But A Better Security Architecture
The hacks aren’t slowing down. At the current pace of crypto hacks, they could reach $4 billion by the end of the year. And to ensure that your current exchange or upcoming exchange in 2025 doesn’t become the victim, you need to partner with a leading cryptocurrency exchange software development company.
Who offers the best security-first cryptocurrency exchange software development services?
Antier offers the best services, whether you need help with securing your existing crypto exchange platform or building a security-first exchange from scratch.
Work with experts who’ve audited, tested, and hardened infrastructure for dozens of exchanges worldwide.
Antier offers:
- End-to-End Secure Cryptocurrency Exchange Software Development
- Penetration testing for CEX/DEX platforms
- Institutional-Grade Custody Integrations
- Secure exchange architecture design
- Smart contract audits
- Incident response readiness kits
Let’s secure your future before some hackers play with it.
Frequently Asked Questions
01. What are the biggest threats to cryptocurrency exchanges in 2025?
The biggest threats include attacks from North Korean state actors, insider threats, vulnerabilities in hot wallets, cross-chain laundering of stolen funds, and the misconception that cold wallets are invulnerable.
02. How much value has been stolen from cryptocurrency exchanges in 2025 so far?
In 2025, $2.17 billion has been stolen from cryptocurrency exchanges, DeFi platforms, bridges, and wallets, marking a 17% increase compared to the total losses in 2022.
03. What is the importance of security in cryptocurrency exchange development?
Security is crucial in cryptocurrency exchange development as neglecting it can lead to significant financial losses and make exchanges prime targets for hackers, who are becoming increasingly sophisticated.







